People are having a big freakout about the Jia Tan user and I want to throw a little napalm on that kitchen fire by showing ya'll what the open source community looks like when you filter it for people with the same basic signature as Jia Tan. The summary here is: You have software on your machine right now that is running code from one of many similar "suspicious" accounts.
We can run a simple scan for "Jia-Tans" with a test Reagent database and a few Cypher queries, the first on just looking at the top 5000 Pip packages for:
- anyone who has commit access
- is in Timezone 8 (mostly China)
- has an email that matches the simple regular expression the Jia Tan team used for their email (a Gmail with name+number):
MATCH path=(p:Pip)<-[:PARENT]-(r:Repo)<-[:COMMITTER_IN]-(u:User) WHERE u.email_address =~ '^[a-zA-Z]+[0-9]+@gmail\\.com$' AND u.tz_guess = 8 RETURN path LIMIT 5000
This gets us a little graph with 310 Pip packages selected:
One of my favorites is that Pip itself has a matching contributor: meowmeowcat1211@gmail.com
Almost every package of importance has a user that matches our suspicious criteria. And of course, your problems just start there when you look at the magnitude of these packages.
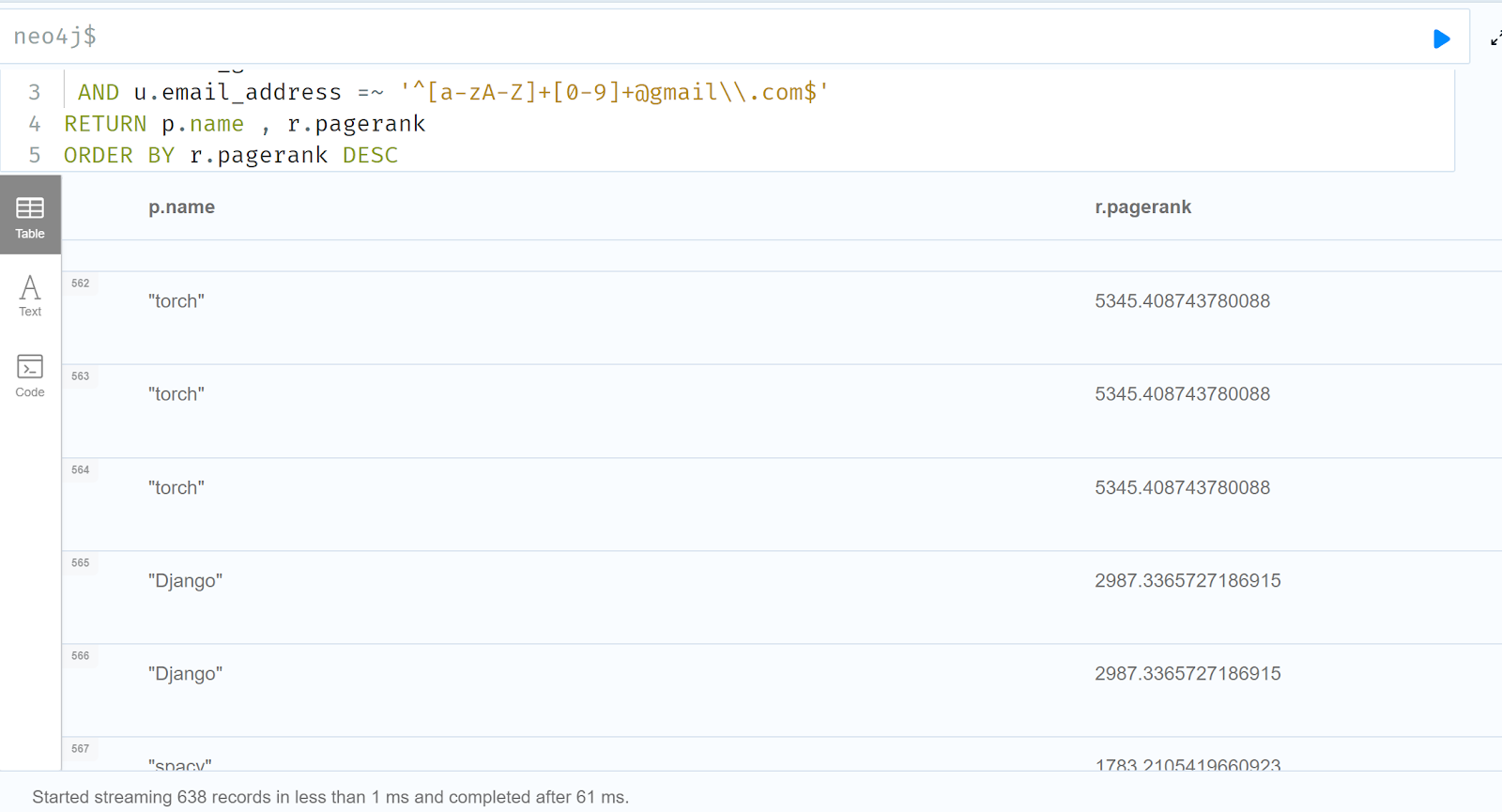
You can also look for matching Jia Tan-like Users who own (as opposed to just commit into) pip packages in the top 5000:
MATCH path=(u:User)-[:PARENT]->(p:Pip)<-[:PARENT]-(r:Repo)
WHERE u.tz_guess = 8
AND u.email_address =~ '^[a-zA-Z]+[0-9]+@gmail\\.com$'
RETURN path
ORDER BY r.pagerank DESC
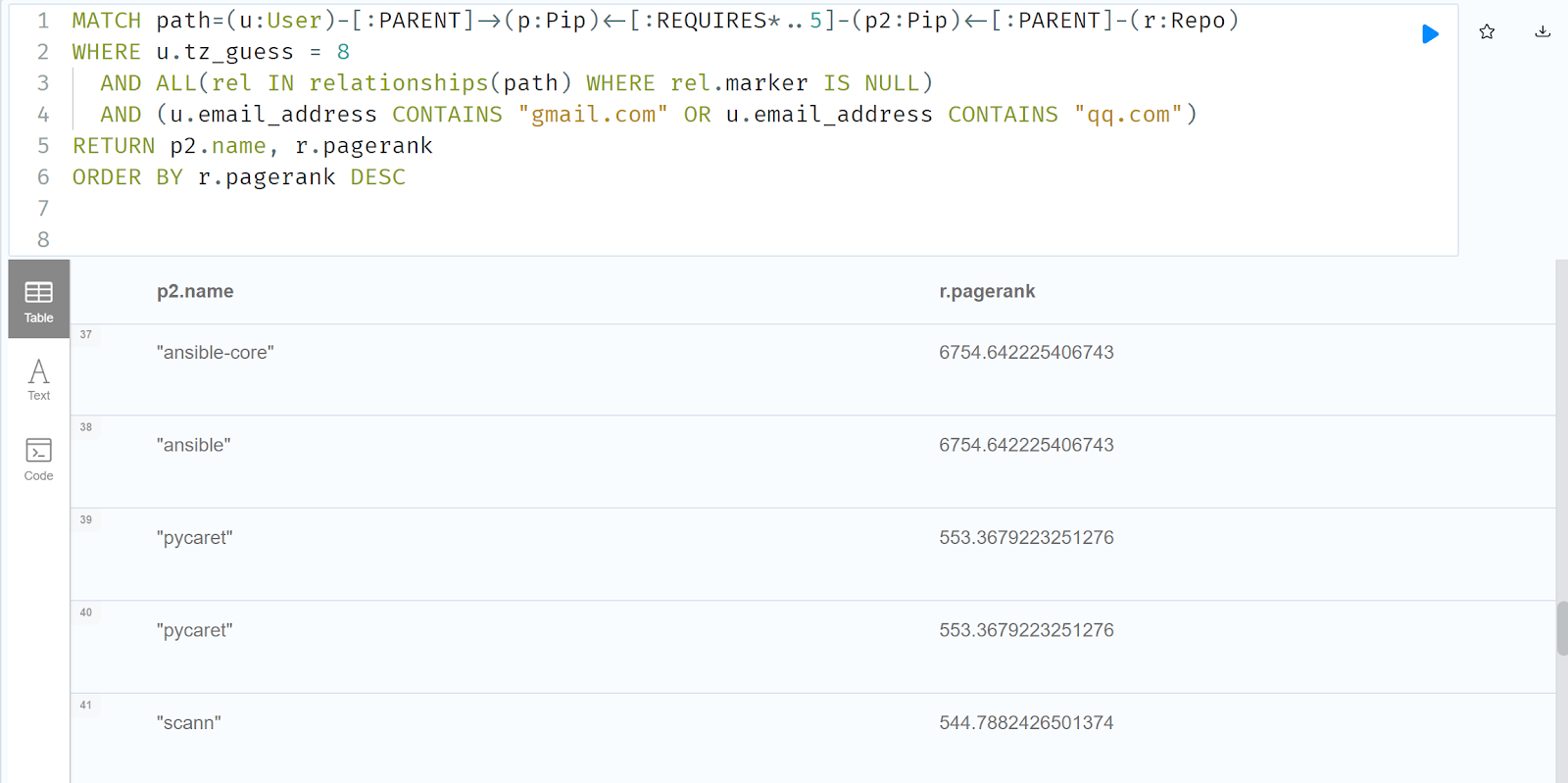
On the other hand, many people don't care about the particular regular expression that matches emails. What if we broadened it out to all Chinese owners of a top5000 Pip packages with either Gmail or QQ.com addresses and all the packages that rely on them. We sort by pagerank for shock value.
MATCH path=(u:User)-[:PARENT]->(p:Pip)<-[:REQUIRES*..5]-(p2:Pip)<-[:PARENT]-(r:Repo)
One of the unique things about Reagent is we can say if a contributor is actually a maintainer, using some graph theory that we've gone into in depth in other posts. This is the query you could use:
Ok, so that's the tip of the iceberg! We didn't go over using HIBP as a verification on emails, or looking at any time data at all or commit frequencies or commit message content or anything like that. And of course, we also support NPM and Deb packages, and just Git repos in general. Perhaps in the next blog post we will pull the thread further.
Also: I want to thank the DARPA SocialCyber program for sponsoring this work! Definitely thinking ahead!





No comments:
Post a Comment